Mimikatz
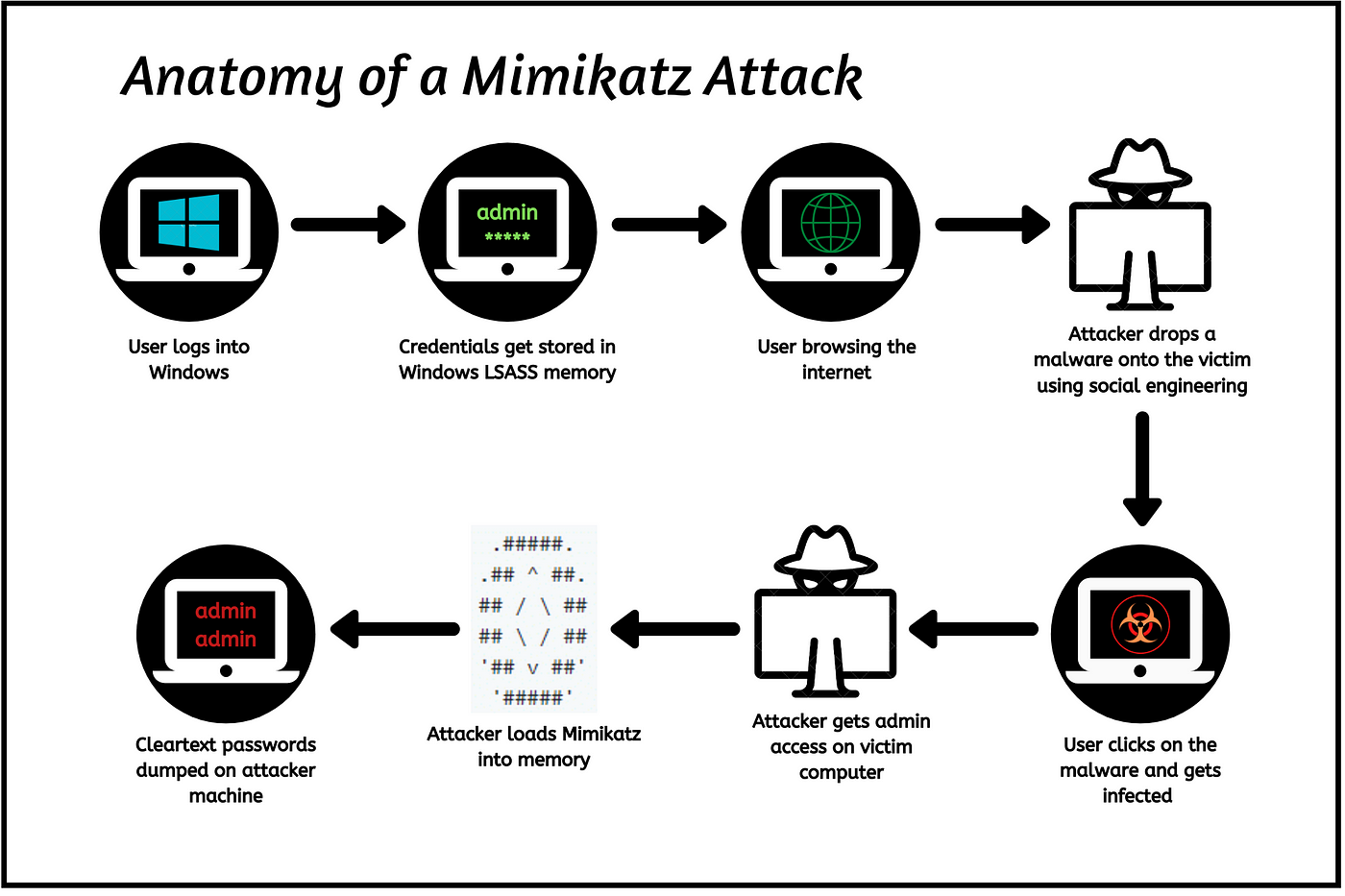
In the intricate landscape of cybersecurity, one tool stands out both for its utility and its potential for harm: Mimikatz. Revered by penetration testers and feared by security professionals alike, Mimikatz is a powerful post-exploitation tool that has left an indelible mark on the cybersecurity landscape since its creation by French security researcher Benjamin Delpy in 2011. This article aims to delve into the multifaceted nature of Mimikatz, exploring its capabilities, applications, and the profound implications it holds for both defenders and adversaries in the digital realm.
Table of Contents
ToggleUnraveling the Secrets of Mimikatz
At its core, Mimikatz is designed to exploit vulnerabilities within the Windows authentication process, particularly focusing on the manipulation of credentials stored in memory. By leveraging a variety of techniques, including pass-the-hash, pass-the-ticket, and golden ticket attacks, Mimikatz enables attackers to extract sensitive authentication credentials, such as usernames and passwords, from compromised systems. Furthermore, it can bypass common security mechanisms, including Windows Defender, making it a formidable adversary in the hands of cybercriminals.
However, Mimikatz is not solely a weapon wielded by malicious actors. Ethical hackers and cybersecurity professionals often utilize Mimikatz in controlled environments to assess the security posture of organizations and identify vulnerabilities before they can be exploited by real threats. Its ability to simulate real-world attack scenarios provides invaluable insights into the effectiveness of existing security measures and helps organizations fortify their defenses against potential breaches.
Despite its dual nature, the widespread availability and ease of use of Mimikatz pose significant challenges for defenders. With the tool readily accessible online and accompanied by comprehensive documentation, even novice attackers can deploy Mimikatz with relative ease, amplifying the threat it poses to organizations of all sizes. Moreover, its ability to evade detection by traditional antivirus solutions underscores the importance of adopting proactive security measures, such as continuous monitoring and anomaly detection, to mitigate the risks associated with Mimikatz-based attacks.
A Double-Edged Sword in Cybersecurity
In response to the growing prevalence of Mimikatz and similar tools, cybersecurity professionals are continuously refining their defensive strategies. This includes implementing multifactor authentication (MFA) to mitigate the impact of credential theft, employing endpoint detection and response (EDR) solutions to detect and respond to suspicious activities, and adopting a zero-trust security model that assumes breach and enforces strict access controls throughout the network.
Furthermore, collaboration between the cybersecurity community and technology vendors is essential to staying one step ahead of evolving threats. By sharing threat intelligence, developing patches and updates to address known vulnerabilities, and fostering a culture of cybersecurity awareness, we can collectively mitigate the risks posed by tools like Mimikatz and safeguard the integrity of digital ecosystems.
Conclusion
Mimikatz epitomizes the dualistic nature of cybersecurity tools – simultaneously serving as a potent instrument for both offense and defense. While its capabilities empower attackers to compromise systems and exfiltrate sensitive data, they also provide invaluable insights for security professionals seeking to bolster their defenses against emerging threats. By embracing a proactive approach to cybersecurity, grounded in collaboration, innovation, and vigilance, we can navigate the complex landscape of digital security and preserve the trust and integrity of our interconnected world.





